As they say, a strong fortress needs a strong foundation. Making a robust platform, with data security at its core, requires us to ensure that every aspect, including how we build-out, is well scrutinized; without compromising on the speed of response and in making innovations both now and in the future.
And that’s why we wanted to talk about DevSecOps.
What is DevSecOps?
DevSecOps is about introducing security earlier in the life cycle of application development, thus minimizing vulnerabilities and bringing security closer to IT and business objectives.
Why are we taking the DevSecOps route?
We are a FinTech company and we work with tons of sensitive data, we have to prioritize security and data management before we begin building the platform. Security cannot be compromised even at the initial stages of any component being built. DevSecOps gives us a standardized process to make sure we don’t overlook security while under pressure to deliver the product.
Illustrating DevSecOps
Here are security aspects covered in various stages of app development:
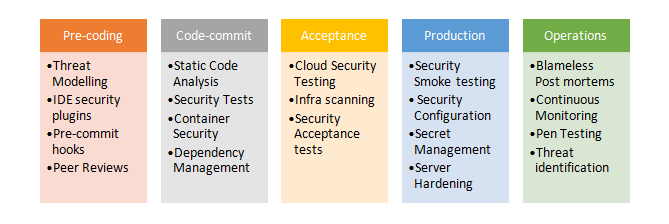
At Fintso we follow Agile and DevOps methodologies.
Given below is the build and deployment process followed with few tools defined.
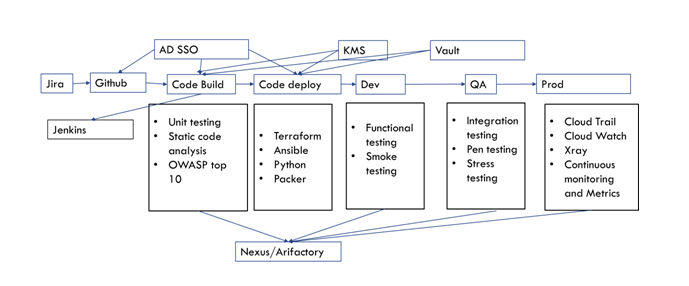
To take an example:
· As the System components are designed, ‘Threat Modelling, for each component takes place to ensure architecturally we don’t leave any security loopholes.
· Once the coding begins based on the design, IDE security plugins run to validate the code that is secured before it is sent for peer review.
· Post completion of peer review, the code is merged and build is triggered where static code analysis, security scans and dependency validations begin.
· Infrastructure as Code follows a similar process of development; the step to acceptance of the security process is covered in the build for infrastructure. The app is then deployed in a QA environment where testing is done. Secret management, Security configuration, and server hardening are part of the Infra code development.
· As a process and guideline, we always keep the secrets in the vault.
· A process is standardized and automated to build a hardened image for VM and Docker.
· RBAC rules take care of security configuration for most parts.
As the logging and monitoring is centralized, all the security-related operational processes are streamlined via tools. These dashboards are actively monitored by the op’s teams.
Other Aspects
These defined steps are from the DevOps process point of view.
The other key aspects of security being looked at are encrypting and controlling the visibility of sensitive data. Making sure if a client is leaving the platform and the user is removed there would be no way to link back to the user or any data still residing in the system.
For the back-office teams to retrieve any sensitive data multiple levels of approvals are needed. The data trail is kept to ensure that the retrieved data is not used for malicious reasons. Adapt employees who have privileges can only access Sensitive Data from company-provided laptops. These devices are configured with DLP, encryption and other security modules.
Detailed Process and Guidelines inculcated in the DevOps cycle to embed security and proper governance
1) Threat modelling is carried out for each service or component being built and integrated. A risk register is maintained based on the risks we identify.
2) Static code analysis for owasp top 10 and other security vulnerabilities would be done.
3) Infrastructure as code undergoes lint and security analysis
4) The OS image or Docker image would pass the security benchmark test before being deployed.
5) Container images and repositories are digitally signed, and images are scanned through tools like Twistlock or Aquasec
6) End-to-end encryption must be configured for any communication between services.
7) Encryption is a must for data in-flight and at rest, the same goes for the backup.
8) 3rd party libraries or other external dependencies are validated to make sure they don't have severely high-security vulnerabilities before use.
9) Defense in depth is followed from the networking aspect. Multiple subnets with necessary firewalls are put in place.
10) Segregation of duties and least privileged access is followed carefully to ensure necessary required access is given through RBAC policies.
11) All higher privileged users must go through MFA.
12) All the external communicating API’s have API gateway with WAF enabled, to ensure throttling, Ddos, or other vulnerabilities cannot be exploited.
13) The environment must be built in a micro services model with immutable services wherever possible.
14) Secrets never go into source code repos. They will be placed in vault and only can be pulled by the code.
15) All logs, audit information and monitoring information come to a central place which is carefully being monitored for alerts and unusual activities.
So, building this vast fortress needs a lot of dedication and care, and someone equipped to deal with the intricacies of data privacy. Because Fintso treads the secure and fortified path of data protection, it is considered one of the best online platforms for mutual fund distributors.
By Ram Ravipati, DevOps Leader, Fintso
Ram Ravipati is the DevOps Lead for Fintso. His experience over the past 18 years has been in leading teams, managing infrastructure, building platforms in the cloud and in implementing DevOps and SRE. This deep understanding is what he is using to build a secure, robust and adaptive platform efficiently keeping in mind the complex yet fast pace of development that we have set for ourselves.
Find out more on our website or Ram's LinkedIn